In modern, decentralized IT environments and modern cybersecurity strategies, the traditional concept of a “trusted network” perimeter is obsolete. Zero Trust Architecture (ZTA) is the strategic security model built to address this reality, operating on the foundational principle: “Never trust, always verify.”
Understanding Zero Trust Architecture
What Zero Trust Architecture Is and What It’s Used For
Zero Trust Architecture is not a single product, but a framework that mandates strict identity verification for every user, device, and workload attempting to access any resource, regardless of its location relative to the network. It assumes that threats exist both inside and outside the perimeter (the “assume breach” mentality).
ZTA is primarily used for:
- Protecting Critical Assets: Securing sensitive data, applications, and intellectual property in highly distributed environments (cloud, hybrid, remote).
- Preventing Lateral Movement: Stopping an attacker who has compromised one endpoint from moving freely to other high-value targets.
- Enforcing Least Privilege Access: Ensuring every entity (user or machine) is granted only the minimum access necessary to perform a specific task.
- Securing Remote and Hybrid Work: Providing granular, context-aware access to resources without relying on vulnerable legacy VPNs.
How Zero Trust Architecture Is Implemented (The Core Pillars)
Implementing Zero Trust Architecture (ZTA) is a strategic journey that shifts the security focus from the broad network perimeter to the individual resource (the Protect Surface). This is accomplished by building security around five core technology pillars, each operating under the principle of “never trust, always verify”.
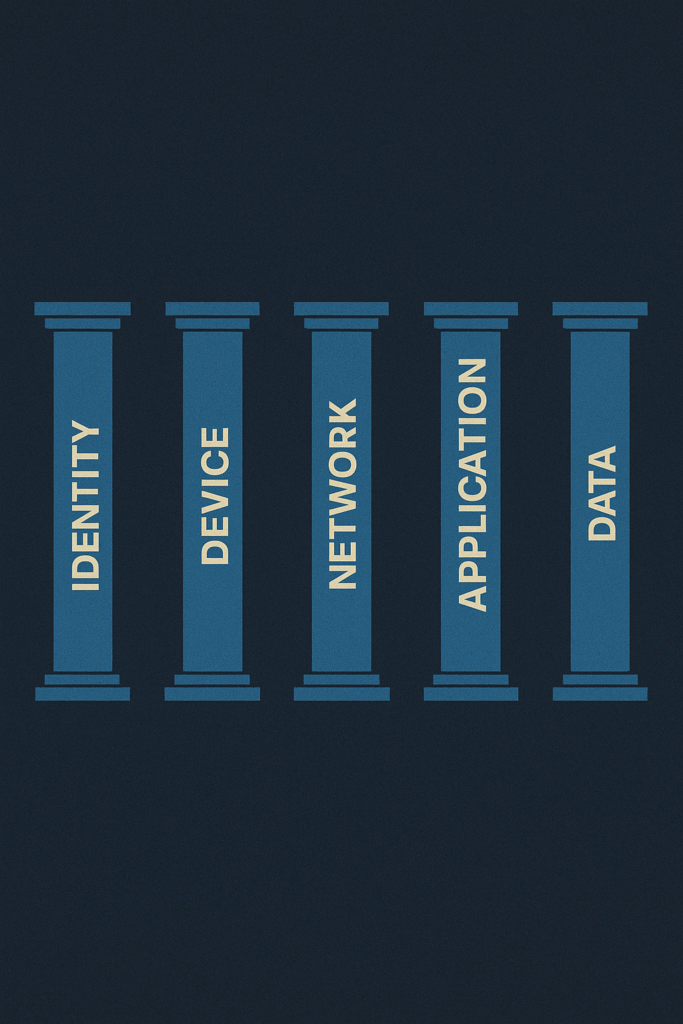
Identity
This pillar is arguably the most critical foundation of ZTA, focusing on the human and non-human entities (users, services, and APIs) requesting access.
Core Principle: Identity is the primary control plane. No access is granted until the identity is strongly authenticated and explicitly authorized. Expansion: It requires moving beyond simple username/password checks. The system must verify who the user is, what role they have, and assess the trustworthiness of the identity session throughout the entire connection. Enforcement: Use of Multi-Factor Authentication (MFA), Single Sign-On (SSO), Privileged Access Management (PAM), and continuous monitoring for unusual behavior (e.g., impossible travel time between logins).
- Key Tool: Multi-Factor Authentication (MFA), Single Sign-On (SSO), and continuous re-authentication.
Devices
This pillar covers all endpoints used to access resources, including corporate-owned and Bring Your Own Device (BYOD) assets, servers, and IoT devices.
Core Principle: The device’s security posture and health must be validated before and during access. A compromised device is considered a threat, regardless of the user’s identity. Expansion: Device validation includes checking for proper configuration, up-to-date patches, disk encryption, and active endpoint protection. If a device falls out of compliance during a session (e.g., antivirus is disabled), access should be immediately revoked. Enforcement: Endpoint Detection and Response (EDR) solutions, Mobile Device Management (MDM), and integration with the ZTA Policy Engine to use device health data as a key input for access decisions.
- Key Tool: Endpoint Detection & Response (EDR), Mobile Device Management (MDM), and continuous posture checks.
Networks/Environments
This pillar recognizes that the traditional network perimeter is obsolete. It focuses on isolating critical resources and securing traffic.
Core Principle: The network itself is assumed to be compromised. Trust is not inherited based on network location (e.g., being on the internal corporate Wi-Fi). Expansion: Instead of securing the entire network, ZTA uses Microsegmentation to divide the network into granular security zones, isolating workloads and applications. This limits the “blast radius” of a breach by preventing lateral movement. Enforcement: Network segmentation gateways, firewalls, and encryption of all traffic (even internal, east-west traffic) to ensure that if a session is intercepted, the data remains protected.
- Key Tool: Microsegmentation, encryption of all traffic, and policy enforcement at the network layer.
Applications & Workloads
This pillar protects the systems, services, and applications that process data, whether they run on-premises or in the cloud (IaaS, PaaS, or SaaS).
Core Principle: Access control must be enforced at the application layer, ensuring users only connect to the specific application they are authorized for, not the underlying network it sits on. Expansion: This is about securing the code, the communication interfaces (APIs), and the runtime environment. Workloads must also be continuously monitored for behavioral anomalies and vulnerabilities. Enforcement: Application security testing throughout development (DevSecOps), API gateways for authentication and rate limiting, and using containers/immutable infrastructure to prevent unauthorized changes.
- Key Tool: Strong application authorization, API security, and securing the software development lifecycle (DevSecOps).
Data
This pillar is the ultimate Protect Surface—the core reason for the entire ZTA implementation.
Core Principle: Data is protected regardless of where it resides (at rest, in transit, or in use). Policies must classify data sensitivity and enforce least-privilege access to ensure only authorized entities can interact with it.
Expansion: Data protection involves inventorying and classifying sensitive information (e.g., PII, financial records). Access policies should be tied directly to the data’s classification (e.g., “Only users with the ‘Finance Manager’ role on a ‘compliant’ device can access ‘Level 1 Financial Data’”).
Enforcement: Data Loss Prevention (DLP) tools, encryption (database, file-level, and transit), and strong access controls integrated with the Identity pillar.
- Key Tool: Data classification, encryption, and Data Loss Prevention (DLP) tools.
The ZTA Process involves mapping transaction flows between these pillars to create dynamic, context-aware access policies that are continuously monitored and enforced.
Real-World Zero Trust Architecture in Action: The Corporate Use Case
To better understand the practical benefits of Zero Trust Architecture, let’s examine a scenario involving a fictional company, Acme Financial Services.
Daily-Life Analogy: The Secure Apartment Building
A basic ZTA principle is applied every day when you use your phone to access a digital service:
- You’re on your phone (Device Trust): The app checks your phone’s biometrics and recognizes the device.
- You enter your password and a text code (MFA/Identity): You prove who you are.
- You access your banking app (Least Privilege): You are authorized to see your bank balance, but you cannot access the bank’s internal payroll server or a different customer’s account data. You get access to one application, not the bank’s entire network.
- The bank detects a suspicious location (Continuous Verification): If you log in to your bank from London, and three minutes later, your session attempts to execute a wire transfer from a completely different, suspicious IP address in Asia, the bank instantly revokes access and sends an alert.
Theoretical Use-Case Scenario: Acme Financial Services
Acme Financial Services uses a ZTA framework to manage access for its 5,000 employees, 50 contract developers, and various cloud applications.
| User/Scenario | Access Request | Traditional Perimeter Security | Zero Trust Architecture (ZTA) |
| Mark (Employee) | Accessing the sensitive customer database from his corporate laptop while traveling. | VPN grants him full network access after initial login. If his laptop is compromised, the attacker can move to other servers. | Requires MFA, checks his laptop’s health (patches, EDR running), and grants access only to the database application via a secure broker. Access is continuously monitored. |
| Lateral Movement Attempt | An attacker phishes Mark and gains his credentials while he is inside the network. | The attacker is now “inside the trusted zone” and can search for the finance server and access HR data. | The attacker is immediately challenged when they try to move from the customer database segment to the isolated HR system segment. The access policy for the HR system specifies “HR Team Only,” denying the compromised Mark’s access request. |
| Contractor Access | A developer needs to update a single piece of code in the inventory system for one week. | Requires complex firewall rules or a full network VPN that could accidentally expose other data. | Access is granted only to one specific source code repository for seven days, and only from a specific IP range and with a MFA key. After seven days, access automatically expires. |
The Benefits and Disadvantages of Zero Trust Architecture
The shift to ZTA is a major undertaking, but its advantages in the current threat landscape are compelling.
Core Benefits of Zero Trust Architecture
| Benefit | Description | Reference to Acme Financial Scenario |
| Superior Data Breach Prevention | Limits the “blast radius” of any breach by segmenting resources (microsegmentation) and eliminating implicit trust. | The attacker who compromised Mark’s credentials was immediately blocked from accessing the HR system, preventing a company-wide data leak. |
| Enhanced Protection from Insider Threats | By continuously verifying all users (even employees), ZTA mitigates risk from compromised accounts or malicious insiders. | Even if a disgruntled employee tries to access an unauthorized system, the ZTA policy engine denies the request due to least privilege and unusual behavior. |
| Granular Access Control | Access is granted only to the specific application or data needed, based on the user’s role and real-time context. | The contractor’s access was limited strictly to the one specific code repository they needed for one week, ensuring no accidental or malicious viewing of other company data. |
| Simplified Regulatory Compliance | Provides comprehensive, verifiable audit trails showing who accessed what, when, and under what conditions, essential for regulations like HIPAA and GDPR. | Acme can easily provide auditors with logs proving that all access to the customer database was verified via MFA and a compliant device. |
| Secure Remote and Hybrid Work | Replaces blanket network access (VPN) with highly secure, application-level access (ZTNA). | Mark can work securely from anywhere because his access is dependent on his device health and identity, not his physical location on the network. |
Key Disadvantages and Implementation Challenges of Zero Trust Architecture
| Disadvantage | Description | Mitigation Strategy |
| Complexity and Cost | ZTA is an architectural overhaul, not a product. It requires significant initial investment in technology (IAM, ZTNA tools) and specialized security personnel. | Implement ZTA in phases, starting with the most critical assets (Acme’s customer database) to demonstrate ROI and manage complexity incrementally. |
| Integration with Legacy Systems | Older, proprietary applications and devices may not support modern identity and authentication protocols, requiring costly workarounds or replacement. | Acme must carefully map transaction flows for legacy apps and use ZTA gateways to wrap them in modern access controls without breaking them. |
| User Productivity Friction | Frequent re-authentication or overly restrictive policies can frustrate employees and lead to pushback. | Utilize adaptive and risk-based access; if Mark is on a trusted corporate device in his office, the system can reduce the frequency of MFA checks. |
| Requires a Complete Mindset Shift | IT and security teams must shift from defending the perimeter to treating every user and packet as a potential threat, which can be a difficult cultural change. | Provide comprehensive training for all employees and IT staff on the “why” and “how” of the new security model. |
By referencing the use-case, it is clear that while ZTA demands initial investment and planning, the long-term benefits of Zero Trust Architecture—specifically its ability to contain threats and secure decentralized resources—are essential for protecting modern enterprises like Acme Financial Services from catastrophic cyberattacks.